by Pablo Moriano
The term “insiders” is widely defined as current or former employees who accidentally or maliciously misuse their trusted access to harm an organization’s assets. According to multiple security reports, a considerable percentage of security professionals from multiple security firms have experienced the theft or corruption of information by insiders. Given the elevated privilege that insiders have in terms of trust and access, insider attacks are often cataloged as one of the most costly and challenging problems in computer security.
Detection of insider threats relies on monitoring individuals and their interactions with organizational resources. Identification of anomalous insiders typically relies on supervised learning models that use labeled data. We can only find the insiders we know how to detect. And even with that, labeled data is not easily obtainable. The labeled data that does exist is also limited by current insider threat detection methods and undetected insiders would not be included. These models also inherently assume that the insider threat does not change, but it could evolve between model generation and use.
Insiders are more likely to attack following the occurrence of precipitating events. Precipitating events are large-scale incidents that cause concerning behaviors in employees and leaves them predisposed to malicious actions, such as layoffs, significant restructuring, and plant or facility closure.
To test this characterization, researchers Pablo Moriano and L. Jean Camp from the School of Informatics, Computing, and Engineering at Indiana University, in collaboration with Jared Pendleton and Steven Rich from Cisco Systems, Inc., have proposed a graph mining framework to quantitatively test and prove this hypothesis. Their proposed method relies on the notion of the community structure of graphs made on engineers/developers interactions derived from a version control system. In an article published in the 9th ACM CCS International Workshop on Managing Insider Security Threats (MIST), they show that variations in the proportion of interactions across different components are correlated with the announcement of precipitating events.
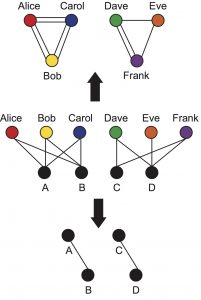
To demonstrate this, the researchers used more than 22 years of data from the interactions between engineers/developers and software components in the Cisco Internetwork Operating System (Cisco IOS). Their modeling framework is based on capturing these interactions using a series of bipartite graphs. From the bipartite graphs, they focus on the interactions between employees using one-mode projection graphs—graphs in which engineers are connected if they have contributed to similar projects. The key observation in their study relies on the idea that engineers used to work on similar or related components during a period of time, with few incidences with non-related components.
At the heart of their method, they identified communities of employees in these graphs to quantify the number of times that engineers begin working on components that they usually used to work compared with the ones that they do not use to work (nominally intra- and inter-community ratio).
They showed that this measure correlates very well with the dates of precipitating events (corresponding to dates of restructuring within Cisco).
They also compared the results of their proposed measure with density-dependent statistics on the graphs (i.e., topological measures that are associated with the volume of interactions) and showed that there is a statistically significant correlation between the occurrence of the precipitating events and the diversification of patterns of interactions of engineers with the software components. This observation was not found as relevant with the density-dependent statistics as intuition might suggest.
The study quantitatively validates a common qualitative hypothesis on a private dataset. The authors state that future work ideally would include a partnership with other organizations to check the correlation with other precipitating events, and then, in the long run, the adoption of this as a mechanism to detect high-risk behaviors by insiders. However, if insider threats are of or in response to specific events, then other events, including employee dismissal, disputes with employers, perceived injustices, family problems, coercion, or new opportunities should be considered when evaluating the proposed approach.
More information: Pablo Moriano et al., Insider Threat Event Detection in User-System Interactions, Proceedings of 9th ACM CCS International Workshop on Managing Insider Security Threats (MIST), Pages 1-12, Dallas, TX, USA, 2017.
doi:10.1145/3139923.3139928